Identification technologies evaluation method: an application in cattle chain
Priscilla Cristina Cabral Ribeiro
priscillaribeiro@id.uff.br
Fluminense Federal University - UFF, Niterói, Rio de Janeiro, Brazil.
Mário Otávio Batalha
dmob@ufscar.br
São Carlos Federal University - UFSCar, São Carlos, São Paulo, Brazil.
Katherine M. Chudoba
kathy.chudoba@usu.edu
Utah State University - USU, Logan, Utah, United States of America.
Deevon Bailey
deevon.bailey@usu.edu
Utah State University - USU, Logan, Utah, United States of America.
Annibal Jose Scarvada
annibal.scavarda@unirio.br
Federal University of the State of Rio de Janeiro – UNIRIO, Rio de Janeiro, Rio de Janeiro, Brazil.
Abstract
The objective of this paper is to apply an identification technologies evaluation method in cattle chain in a sample in Brazil and in USA. These technologies are information and communication technologies, such as Radio Frequency Identification and barcode. The research methodology used was a qualitative study, with an extensive literature review on information technology, information systems, and Radiofrequency evaluation methods. A scale was created to decide what decision the case study has to take according to its technology. The method proposed can contribute to the theory of information technology evaluation and can offer practitioners an efficient and effective way to evaluate prospective information technology implementations. The rankings showed that American respondents evaluate RFID with a better performance in security variables. Brazilian agents evaluate Radiofrequency with a better performance in technical and organizational variable. The scale revealed that the Americans have more agents in Group B (8), which means reevaluation of the identification method, and just one in Group A, meaning that it has to change its information technology. Brazilian agents have more cases in Group B (6), than group C (3), and Group A (1). This means that the majority of the sample has to reevaluate their method to trace cattle.
Keywords: Evaluation method; Identification technologies; Information Technology; RFID.
1 Introduction
Information Technologies (ITs) are important tools that facilitate positive relationships between members of supply chain (SC) networks. For instance, they help to integrate work activities among primary and supporting members of a SC. The basic purpose of technologies such as Radio Frequency Identification (RFID) is simply to identify an object, and to provide data about its source, production date and expiration date.
Albertin et Albertin (2008) emphasize the IT evaluation using metrics to analyze its success and to establish a framework to evaluate the investments. According to these authors, three dimensions have to be considered: strategic value, organizational value and the business value. This evaluation requires metrics, which have to be analyzed before the IT implementation. Grover et al. (1996) suggested an evaluation to avoid mistakes that are made when the managers give the value to an IT (improving or decreasing their value). These mistakes produce problems for the manager who is leading the effort to invest in IT. Therefore, the performance criteria have to be used in an appropriate way in different situations (e.g., the acquisition, the project and actual use) and by different agents (e.g., users and managers).
A unique contribution of this different approach to IT evaluation is its technical and organizational focus. Some methods focus on financial aspects; however, this paper presents variables that lead to a broader discussion. The method is a contribution to the literature on IT/IS evaluation methods, updating previous methods and providing guidance to researchers and practitioners. The majority of IT/IS evaluation methods include financial variables and some of them do not consider other variables, as this evaluation method does. By using the method presented in this paper, companies can better understand their IT weaknesses, become aware of new opportunities to implement other IT; and learn how to implement these IT and how to relate them to other activities in the company such as logistics.
Identification technologies, as RFID, specifically ear tags, are used to monitor the supply chain and are critical in terms of providing the capability to track goods and to control inventories throughout the world (Ribeiro et al., 2011). In cattle chain, tracking systems constitute control methods, since they can be used to identify the operations and ranches through which the animals have passed. In addition, they can be used for responding to infectious diseases and identifying the responsible party in the event of contamination amongst the cattle (Ribeiro et al., 2009).
The objective of this paper is to apply an identification technologies evaluation method in cattle chain in a sample in Brazil and in USA. In addition, the final method has three sets of variables in its framework: organizational, security and technical. The method has a specific objective, which is not to present a financial approach, but managerial and technical approaches to the IT evaluation.
Why do the companies have to implement ITs such as RFID? What benefits will the technology provide to compensate for its cost? While the cost of RFID has decreased since the 1990s, its implementation still demands changes in organizational processes and even in the physical layout of facilities. Identification technologies such as RFID and barcode require an evaluation to determine the right moment to implement them and to answer the question: Will this IT produce benefits that compensate for investments in money, human resources, and time? The evaluation method presented next identifies three sets of variables that will help answer this and other relevant questions.
The paper is comprised of five sections that describe the objective of the paper, its justification, and the question, followed by sections that describe the literature, research method, the evaluation method, the results, conclusion, and recommendations.
2 Literature review: the ID technologies evaluation method
2.1 The organization of variables
This paper relies on the analysis of an extended literature review about IT and information system evaluation methods and models. We identified three major categories of variables: organizational, IT safety and technical aspects. The first group, organizational variables, is divided into four smaller categories: relative advantage, compatibility, observation, complexity, and trialability (Rogers, 1995). The key objectives of a business make up the fourth category. These objectives were described by Tallon et al. (2000) as a benefit for efficiency, effectiveness, reach, and structure.
The second group of variables consists of IT safety variables (also evaluated using standard scales), and includes confidentiality, data integrity, physical integrity, availability, and consistency.
The third group, technical variables, includes procedural aspects like reliability, complexity, experimentation, environmental aspects, and economic aspects – all of which can be further broken down and examined.
One group of variables that is not considered as the others, because it must be applied during all steps of implementation, is the steps of an information system (or technology) evaluation, which include: implementation, pre-implementation, post implementation and post mortem. (Beynon-Davies et al., 2004). The divisions of each set of variables will be explained in the next item.
2.2 Literature review: Information Technology, Information Systems and RFID evaluation methods
DeLone et McLean (1992) presented their IS Success model, in which they identified key variables relevant to IS evaluation. Their seminal work provides an overarching framework to study IS evaluation.
Ahituv (1980) concluded that IS has a great number of evaluation methods, but these methods have problems with a scarce and scattered theoretical background as well as severe technical problems in terms of measurement. We now draw on the work of more recent research to address these concerns and enhance DeLone et McLean’s foundational work.
2.2.1 Technology Evaluation
We begin our discussion with Rogers’ work (1995) because it is relevant to identification technologies as technology innovations. Rogers (1995, p. 206) explains the rate of adoption of an innovation by “five attributes: relative advantage, compatibility, complexity, trialability, and observability.” The method present in this paper considers these attributes as main variables (Table 1).
The first sub-variable, Relative Advantage, has been investigated by other researchers. Sonnenwald et al. (2001) divided Relative Advantage into work goals, quality of work outcomes, adding convenience and social prestige provided by the innovation. These sub-variables were interpreted by the authors of this paper such as Goals Support, Quality of Results, High Rank Achievement and Maintenance.
Sonnenwald et al. (2001) divided compatibility into participation in a group, communication in a group, experiences with communications technology in a group setting, and user needs related to general system qualities, such as reliability and response time. This set of variables was used in this paper; however, ‘participation in a group’ and ‘user needs related to general system qualities’ were not included in this method because their meaning will guide them to other areas of focus (e.g., more managerial than technical). Other authors studied compatibility, such as Bailey et Pearson (1983), Srinivasan (1985), and Moore et Benbasat (1991).
Complexity was divided into ease of use and ease of learning a system. Trialability is renamed in this paper as “experimentation” and includes ease of data recovery and efforts to use the system. Observation includes variables of results demonstrability and visibility. (Sonnenwald et al., 2001). In this paper, just visibility was included to describe observation because quality of results (one of relative advantage sub-variables) has the same meaning.
Boynton et al. (1994) considered some constructs and one of them, strategic planning, was associated with Goals Support. Sedera et al. (2004) built a model where they included a set of measures named Organizational impacts, which can be considered as Quality of Results. Clemons (1991), in his paper about evaluation of strategic investments in IT, contributed to the method evaluation when he suggested High Rank Achievement and Maintenance in the sub-variable Relative Advantage. He concluded that IT has become a ‘strategic necessity’, but not a source of competitive advantage.
Agarwal et Prasad (1997) built a model, which has several innovation characteristics: relative advantage, ease of use, compatibility, trialability, visibility, result demonstrability and image. Moore et Benbasat (1991) and Agarwal et Prasad (1997) discussed IT Experiences in their papers, and Sonnenwald et al. (2001) discussed the Compatibility variable in their paper. Bailey et Pearson (1983) contributed the sub-variable Reliability and Response Speed/Time defining Reliability as “the consistency and dependability of the output information”, and Timeliness such as “the availability of the output information at a time suitable for its use.” Related to this sub-variable, Ahituv (1980), Srinivasan, (1985), Miller et Doyle (1987), Mahmood (1987), Slevin et al. (1991), Bradley et al. (2006), Sabherwal et al. (2006), Petter et McLean (2009), Igbaria et Tan (1997), and Petter et al. (2008) discussed it in different ways, but the main idea is the relationship of timeliness-reliability and response speed.
Group Communication and “the extent of information sharing between providers and users” are other attributes from Sonnenwald et al. (2001), which were also discussed by other researchers (Boynton et al., 1994; Bailey et Pearson, 1983; Agarwal et Prasad, 1997).
Mahmood (1987) contributed with Complexity, such as Sedera et al. (2004), DeLone et McLean (1992), and Wang et Forgionne (2008), writing about ‘Ease of Learning the System’, that is included in this group. Davis (1985), Moore et Benbasat (1991), Agarwal et Prasad (1997), Igbaria et Tan (1997), Sabherwal et al. (2006), Petter et McLean (2009), Wang et Forgionne (2008) and Petter et al. (2008) contributed to this group complexity when they included the variable ease of use in their models. Sabherwal et al. (2006) wrote about effort to use the system as did Wang et Forgionne (2008).
Moore et Benbasat (1991, p. 215) and Agarwal et Prasad (1997:562) considered trialability as an experimentation in their model, where they joined it with observation from the potential adopters’ point of view.
The sub-variable observation skill has one variable that is interpreted as visibility. Moore et Benbasat (1991) and Agarwal et Prasad (1997) extended the discussion including other variables; however, all of them wrote about visibility in their papers.
2.2.2 Information Technology Evaluation
The Information Technology Security Evaluation Criteria – ITSEC UK - was created by the Department of Trade and Industry (1991) to evaluate IT safety. The main aspects of IT shown in this research are confidentiality, integrity (data and physical), availability, and consistency (that has been interpreted as accuracy).
Bailey et Pearson (1983) and Slevin et al. (1991) contributed with these aspects of security, as Lewis et al. (1995) discussed confidentiality. The first authors also included a discussion on integrity.
Srinivasan (1985), Slevin et al. (1991), Sedera et al. (2004) and Bradley et al. (2006) included in their analysis the variable of availability.
When Ahituv (1980), Mahmood (1987), Igbaria et Tan (1997), Bradley et al. (2006), Wang et Forgionne (2008) and Petter et McLean (2009) discussed IS evaluation, they focused on accuracy.
According to Tallon et al. (2000), companies have objectives for IT: efficiency, effectiveness, reach, and structure. Sedera et al. (2004) and Petter et al. (2008) also presented effectiveness in their paper. Remus (1984), Boynton et al. (1994) and Sedera et al. (2004) considered variables related to efficiency, which lead us to add efficiency to our evaluation method.
Bailey et Pearson (1983), Rivard et Huff (1984), Mahmood (1987), Igbaria et Tan (1997), Millman et Hartwick (1987), Miller et Doyle (1987), and Wang et Forgionne (2008) related IS effectiveness and efficiency in their models to some variables in different ways.
When Boynton et al. (1994) explained cost reduction, management support, strategic planning, and competitive trust, they made some associations, such as cost reduction with efficiency; strategic planning with goals support; and competitive trust with reach.
2.2.3 Information System Evaluation
Beynon-Davies et al. (2004) presented four kinds of IS evaluation procedures based on the IS lifespan. These procedures are: strategic evaluation, constructive evaluation, cumulative evaluation, and post-mortem. The strategic evaluation is used sometimes for the pre-implementation stage, and includes IT/IS investments, considering the comparison between potential and estimated costs. The constructive evaluation determines the IS’s importance and value during its development. The cumulative evaluation, which is done after the implementation of IS, in the post-implementation stage includes the investment and benefits return established by the strategic evaluation after the period of use of an IS. Finally, the post-mortem evaluation is performed after the company discontinues a project totally or partially. It is actually a variation of the cumulative evaluation.
Grover et al. (1996) and Franz et Robey (1986) did not describe these types of evaluation as Beynon-Davies et al. (2004) did; however, they discussed the stages of implementation and categories of evaluation.
2.2.4 RFID Evaluation
Deavours et al. (2005) used some aspects to evaluate RFID tags: productivity (i.e., it establishes the number of labels that are actually working) and variation (i.e., the difference in performance between labels of the same model). To measure information accuracy, Morey (1982) presented variables measuring errors: the transaction reject rate, the intrinsic transaction error rate, the stored Management of Information System regarding to technical aspects, and performance and uniformity.
Miller (2007) compared twelve different categories of labels using some variables and divided RFID evaluation into three different aspects: environmental, economical, and technical. The variables included performance in noisy areas (since they may interfere with wireless or powerless technologies), reading rate, performance close to water or metal, technology maturity, operational quickness, and cost (hardware/labels).
Relating to economic issues, the cost-benefit relationship and profitability were considered by researchers such as Rivard et Huff (1984), Ein-Dor et al. (1981), Hitt et Bryjolfsson (1996) and Sedera et al. (2004). Ein-Dor et al. (1981) developed three measures of profitability: budget, resource requirements and cost savings. Miller (2007) considered company budget to decide whether RFID should be implemented or not. Sedera et al. (2004) measured Enterprise System Success (ESS) related to costs too. Hitt et Bryjolfsson (1996) considered other two measures of IT value: productivity and consumer surplus. According to these researchers, it is possible for firms to realize productivity benefits from effective management of IT, without seeing these benefits translate into higher profitability.
Related to the technical aspects, the issue has been evaluating technology often enough to ensure its conformity with the standards available. Deavours et al. (2005 B-43) noted that “the tolerance of the tag to water correlates to free space performance metrics.” The sub-variable Variation was considered by Morey (1982) and Deavours et al. (2005) and it is included in this method to show how boxes or tags are different from the others. The authors cited above contributed to the set of variables presented in the model built in this paper. These contributions are summarized in Table 1.
Table 1. Variables and authors of evaluation method
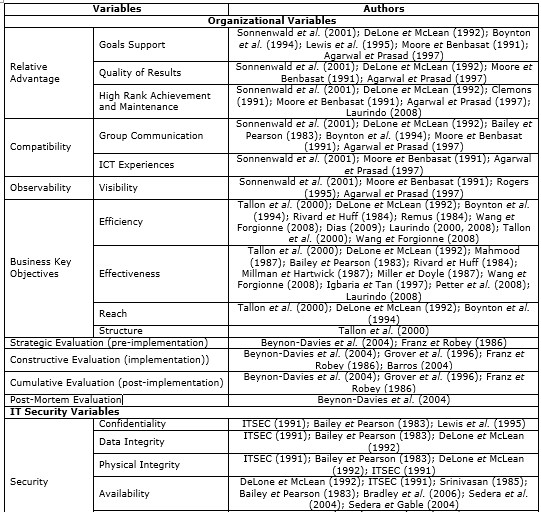
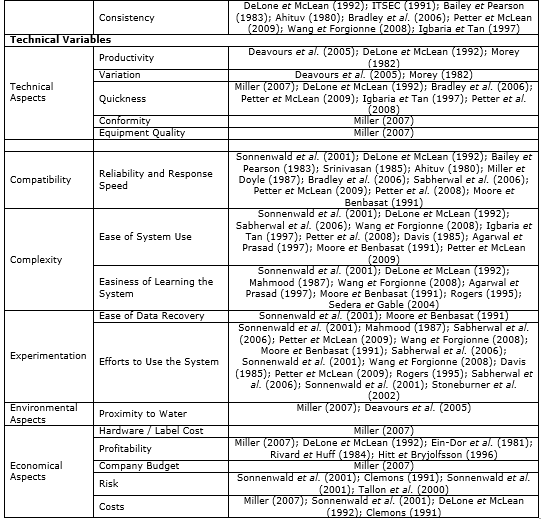
Source: The authors’ own
3 Method
In this research, the qualitative approach was adopted since the objective is to gather information through interviews including the interviewees’ opinions and views (Bryman, 1989). The case study method was chosen because the focus is on how much the ranches nowadays use Information Technology. The research was carried out using a small number of cases, but thoroughly for all ranches studied, and it does not allow for generalizations (Yin, 2001).
The research instrument was semi-structured interviews with closed and open answers (yes/no questions ranked on a 5-point scale, where 1 is “very low” and 5 is “very high”). The respondents are the owners and operators of ranches, and managers and similar positions in industries (harvest facilities).
The evaluation variables are the basis of the IT evaluation method developed by the authors based on the literature review. To make it easy to understand, in the method developed by the authors, the variables were organized differently. Some variables that are normally grouped together belong to a different group now. The Cronbach’s Alpha was used to test the reliability of the questionnaire, and the procedure output has an alpha of 0.81 for the first group of variables (organizational variables), an alpha of 0.85 for the second group (IT safety), and an alpha of 0.82 for the third group (technical variables). These are good results considering that 0.70 is the acceptance cutoff value (Santos, 1999).
Thus, the first group, ‘Organizational Variables’, is divided into four small groups. The first one is the relative advantage, which is related to the rate of technological innovation used by the company, and which was, in turn, divided into three contributions provided by innovation (ranked according to the respondent’s answers): company support in order to meet the goals, assurance that the company has quality results, and achievement and maintenance of high ranking in the market. For the attribute of compatibility – the second group - which is related to the company missions and objectives, IT was evaluated according to its contribution towards the group communication and experience with communication technology. The company’s observational ability is related to the last attribute, and the third group, which is innovation visibility in the market (if the technology used by the company in the supply chain gives it a visibility in the market, the respondent will mark “5” on the scale above). The business key objectives compose the fourth group, and were translated by Tallon et al. (2000) into IT and were ranked according to the same scale used before. Thus, IT was evaluated as a benefit for efficiency, effectiveness, reach, and structure.
The second group of variables is ‘IT Safety Variables’, which was evaluated using the same scale as before, considering mainly confidentiality, data integrity, physical integrity, availability, and consistency.
The third group, ‘Technical Variables’ includes technical aspects, reliability, complexity, experimentation, environmental aspects, and economic aspects. Technical aspects contain productivity, variation, quickness, conformity, and equipment quality. Reliability is a group that has some variables to evaluate the IT such as reliability and response speed. For the complexity group, the evaluation items were: ease of system use and learning. Experimentation is a group, which was divided into ease of recovering data, effort required using the system, risk involved, and costs. Environmental aspects include ‘closeness to water’ in order to evaluate the resistance of the RFID ear tags to some materials, which are present in the place where cattle is. Economical aspects include hardware (label) cost, profitability, and company budget.
In Brazil, the case studies were carried out in six ranches in São Paulo, Mato Grosso, and Mato Grosso do Sul, and four industries in Mato Grosso do Sul, Minas Gerais, and São Paulo. The case studies were carried out in seven ranches in Utah and Wyoming, and two industries in Utah and Washington in the United States.
Tables present in the next item show the averages from each group of variables rankings. The authors created a scale in order to decide about the RFID implementation. After, an average was calculated for each group of variables. These averages have their sources from case studies’ rankings.
The respondents were divided in Brazilian and American. The group of ranchers can be divided in two groups: the first one is the group that does not have RFID ear tags in their animals; the second group is one that has RFID ear tags implant in animals’ ears. All the industries used barcodes, so they are in the same group.
The respondents were chosen according to their knowledge in terms of RFID and position in ranches and industries. To avoid a partial interpretation, consumers and suppliers were interviewed, to make a triangle. In this paper, just the consumers are present, to reach its objective (Voss et al., 2002). The information about case study research is presented in Table 2:
Table 2. Field research

Source: Compiled from Rossi (2008)
The sample is in Table 3, where the information about country (Brazil or USA), the agent in cattle supply chain (ranch or industry), the number, the location, and the use of RFID is presented.
Table 3. Sample of the research
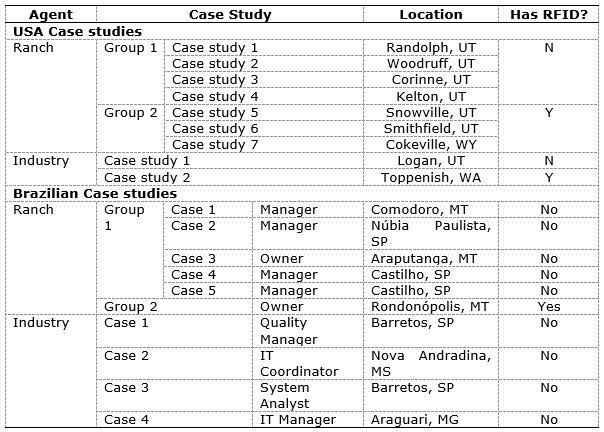
Source: The authors’ own
After the comparison among all cases, a comparison per Sets of variables was carried out and, as a consequence, their averages per case study, per set of variables. The evaluation was done individually and a scale was created based on the same scale used in the questionnaires. The sample was divided in three groups in this scale, as it showed below:
-
Group A → 1 to 2,5 – change the identification method;
-
Group B → 2,6 to 4,0 – re-evaluated the identification method;
-
Group C → 4,1 to 5 – maintain the same identification method.
4 Results and Discuss
4.1 Rancher’s Case studies
American ranchers were divided in two groups because some of them have plastic ear tags (group 1) and some have RFID ear tags (group 2). The industries were together, because both did not implement RFID in their facilities.
In Brazil, ranchers were divided in two groups, from case 1 to case 5 they are in the first group, where the RFID was not placed. On the other hand, case 6 implemented RFID in its operations, thus this ranch was evaluated apart. The Brazilian industries did not implement RFID, so all of cases are in the same group.
4.1.1 American case studies
As explained before, in method, all respondents ranked the variables, and the companies are compared according to the average per set of variables, as Tables 4 to 6 show. Table 4 shows the averages and the evaluation per case in the first group of ranchers:
Table 4. Evaluation per case – American ranchers that does not use RFID
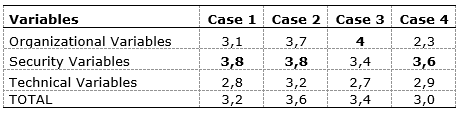
Source: The authors’ own
For Cases 1, 2, and 4, the identification technology used by them has a better performance in terms of security aspect. For Case 3, it is better for organizational variables, since it has a high performance in this aspect. According to the averages all cases are in Group B, which means that these ranchers have to re-evaluate their identification methods. This is an interesting conclusion, because some Cases such as Case 2 and Case 4 are open to introduce new technology in their operations.
Table 5 shows the averages and the evaluation per case in the second group of ranchers:
Table 5. Evaluation per case – American ranchers that use RFID
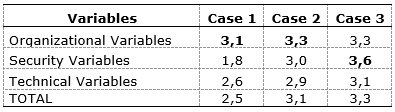
Source: Authors’ own
Even though RFID is safer than barcode, just Case 3 recognizes this characteristic of that IT. Cases 1 and 2 consider RFID as an IT to support the organization and its management. In this group, Case 1 is in the Group A, which means that this rancher has to change the identification method. This issue can be confirmed by the discussion during the interview when the rancher said that he had twice the RFID ear tags and this research considers this rancher as a RFID user; however, he decided to change and return to plastic ear tags. Cases 2 and 3 are in Group B where cases have to re-evaluate their identification methods. Both cases are using RFID, but plastic ear tags, too. Then, there should be a time to decide what method they have to use and not mix them.
Table 6 shows the averages and the evaluation per case in the group of industries:
Table 6. Evaluation per case – American industries
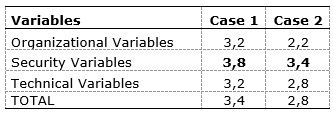
Source: The author(s)’ own
In this group both Cases consider RFID an IT with a better performance in security variable. They are in Group B, which means that these industries have to re-evaluate their identification method. Case 1 should change IT method because this company has financial resources and organization enough to support the RFID ear tags system. In addition, it has suppliers that have RFID ear tags in their cattle, thus it could be easier to use this identification in the barcode place. Case 2 is the same case as Case 1 in the second group of ranchers. It had the RFID system; however, its use was discontinued. Then, the scales show that this industry has been doing the right thing, re-evaluating the use of RFID, even though it is interested to use this technology again.
4.1.2 Brazil case studies
In Brazil the same division was necessary (Tables 7 to 9), because cases from 1 to 5 are ranchers where RFID was not implemented; they are in Group 1. The case 6, whose owner implemented RFID, is included in Group 2. The averages per group of variables are showed in Table 7:
Table 7. Evaluation per case – Brazilian ranchers that do not use RFID
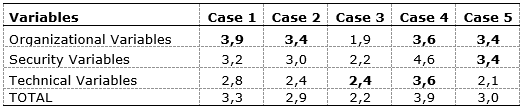
Source: The author(s)’ own
For these ranchers, RFID has a better performance in terms of organizational aspects (4), though some cases have the same average in the other groups. According to the average, four cases are included in Group B, which means that these ranchers have to re-evaluate their identification methods. Case 3 is included in group A, where the customer has to change the information technology. This is an interesting issue, because the respondent is a ranch owner and a manager in one of the facilities of an industry present in this study.
Table 8. Evaluation per case – Brazilian ranchers that use RFID
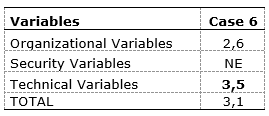
Source: The author(s)’ own
Case 6 has its averages from its rankings shown in Table 8, where the average informs that the case study has to re-evaluate its information technology. This issue was influenced by the absence of ranking in one of the groups of variables. The expectation was to be in Group C, where the company does not have to change or evaluate the IT implemented. In addition, for this case study, RFID is more efficient in terms of technical aspects than others are, though the respondent did not answer the questions related to security variables.
Table 9 shows the averages and the evaluation per case in the group of industries:
Table 9. Evaluation per case – Brazilian industries
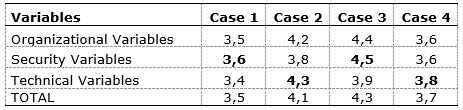
Source: The author(s)’ own
In this group of industries, half of them consider RFID better in terms of security aspect, and the other cases consider for technical issues. Cases 1 and 4 have to analyze the other ITs for traceability and identification. This issue fits their realities, because both of them have interest in implementing RFID, though Case 4 intended to apply a different method to trace the cattle, using DNA, not RFID. Cases 2 and 3 have to maintain their ITs, because, for them, barcode was operating well.
5 Conclusion
RFID is an information and communication technology, which has been used by companies to trace products from the origin to the destination in a supply chain. The implementation of this ICT implies investments in software, hardware, and devices such as readers, antennas and the electronic tags. Because this set of technologies is necessary to use RFID and is expensive, some companies postpone its implementation. This postponement happens because these companies just consider the technology costs and they do not do a deep analysis on costs and benefits.
According to some authors who study IT/IS evaluation models, when a company does not do a proper evaluation prior to implementing an ICT, the technology can be overvalued or undervalued. Both of these situations could generate losses for the companies because, when an IT is implemented by a company, some relationships are generated. One of them is the relationship between employees and the ICT, which may not be easy and depends on the organizational culture, the employee’s level of education, and the knowledge of these employees on how important the ICT is to the company’s operations. Then, companies have to invest time to evaluate their investments in IT because of this high tech – high touch relationship in their SCM.
The beef cattle chain is a good example about this relationship between IT, companies, and people. This supply chain is composed of ranchers, feedlots, industries (harvest facilities), retailers, and final customers. Each of these agents has its own requirements and demands about food safety and quality. It may not be easy to implement an ICT, such as RFID in these companies.
The American and Brazilian traceability systems are not mandatory for RFID, but the market is demanding more control. Because of this, ranchers, feedlots and industries are investing in tags, equipment and software to control better their animals and/or products.
Some ranchers have knowledge about IT, and they have software and RFID technology in their operations to control the cattle and to provide more information to feedlots. Although they have IT in their ranches, they complain about lack of information feedback from their customers. Some top executives in harvest facilities have the same complaint. They agree that IT provides integration in a supply chain, but not in cattle supply chain. They spend effort to develop software and strategies internally and intend to develop a closer relationship (and in the future, partnerships) with their customers. Agents can lose this effort when they are not integrated.
This lack of feedback may be the consequence of the absence of trust. Perhaps some agents in cattle supply chain do not trust other agents. Unfortunately, in some supply chains, companies compete with their suppliers and customers, and this behavior leads them to isolation and to a decrease in market share. This lack of feedback and trust in the supply chain means that the agents do not help to each other, exchange resources or create common solutions to their problems (training, income, and technical supports). The result is less integration and an underperforming supply chain.
The sample showed that in the cattle supply chain it is difficult to have integration and share information between agents. IT exists and all of interviewees recognized its value in this function. Some of these ranchers and industries complain about the feedback of their cattle’s data from the following agent in this supply chain. When they answered about their partnerships that do not exist in most cases, the absence of integration can be observed not just between cattle’s sellers and buyers but among these agents and other in the cattle chain.
The use of IT is in a low level because, as answered by the interviewees, the culture of ranchers and the qualifications in this chain is still low. The cattle chain agents do not have much information about IT and the consequence is that they are not motivated to implement it in their ranchers. As occurred in the Brazilian industry, the manager that works in a sector to sell cattle does not have much information about IT, which shows how this kind of industry is still divided in departments and they are not integrated.
Some ranchers demonstrated knowledge about RFID and some technologies, since they are using or used it. Although they implemented it in their ranches, they do not know and are not using other devices to read the tags. In fact, they have RFID ear tags but they are using plastic ear tags together or until the animals go to the feedlots to control the cattle. The use of RFID is just to turn easy the feedlots’ work, not for their control.
RFID ear tags were considered easy to use, learn and not too much expensive; however, the problem is related to some technical aspects and training. The companies that sell these tags have to provide better support to the ranchers and the purchasing companies, such as Case 2 in industry’s sample, which have to follow all technical instructions (as purchasing the right equipment to read the tag) in order to have a good result of these tags.
The majority of the sample answered that differentiated products and mandatory systems are reasons that can lead ranchers and industries to invest in new technologies. Then, the American government and all cattle supply chain agents have to further discuss about these necessities in this product chain.
The individual rankings were analyzed and showed that some groups have to re-evaluated, and one rancher has to change the identification. These discussions show that some ranches and companies were right; thus, they decided to change the method and re-evaluate their use of RFID ear tags, and, in Brazil, the agent who had implemented RFID in his operations maintain this ICT to trace cattle and the final products. According to these results, an evaluation is necessary, as some authors write in their papers (in literature review), and as the case studies show in the field research. The issues from the rankings represent the concerns from the American and Brazilian agents. The majority of the Americans gave higher values to RFID in terms of security variables, which means that the ICT is not meant to be used to increase their earnings, and they are not concerned about the mandatory system. Brazilian agents evaluate RFID with a better performance in the technical and organizational variables, because, except for one case study (industry) that had problems with information security, all of them expect more control for their raw material and final products.
References
Agarwal, R.; Prasad, J. (1997), “The Role of Innovation Characteristics and Perceived Voluntariness in the Acceptance of Information Technologies”, Decision Sciences, Vol. 28 No. 3, pp. 557-82.
Ahituv, N. (1980) “A systematic approach toward assessing the value of an information system”, MIS Quarterly, Vol. 4, No. 4, pp. 61-75.
Albertin, A. L.; Albertin, R. M. M. (2008), “Benefícios do uso de tecnologia de informação para o desempenho empresarial”, Revista de Administração Pública, Vol. 42, No. 2, pp. 275-302.
Bailey, J. E.; Pearson, S. W. (1983), “Development of a tool for measuring and analyzing computer user satisfaction”, Management Science, Vol. 29, No. 5, pp.530-45.
Beynon-Davies, P. et al. (2004), “Information systems evaluation and the information systems development process”, Journal of Enterprise Information Management, Vol. 17, No. 4, pp.276-82.
Boynton, A. C. et al. (1994), “The influence of IT management practice on IT use in large organizations”, MIS Quarterly, Vol. 18, No. 3, pp.299-318.
Bradley, R. V. et al. (2006) “Information system success in the context of different corporate cultural types: an empirical investigation”, Journal of Management Information Systems, Vol. 33, No. 2, pp. 267-94.
Bryman, A. (1989), “Quantity and quality in social research”, in: Bulmer, M. (Ed). Research Methods and Organisation Studies, Unwin Hyman, London, pp. 135-69.
Clemons, E. K. (1991), “Evaluation of strategic investments in information technology”, Communications of the ACM, Vol. 34, No. 1, pp. 22-36.
Davis, F. D. J. (1985), “A technology acceptance model for empirically testing new-ender user information systems: theory and results”, Dissertation, The Sloan School of Management, Massachusetts Institute of Technology, Cambridge, Massachussets.
Deavours, D. et al. (2005), “RFID performance tag analysis”, The University of Kansas: Information and Telecommunication Center, pp.51, Technical Report, ITTC-FY2006-TR-40980-01.
DeLone, W. H.; McLean, E. R. (1992), “Information systems success: the quest for the dependent variable”, Information Systems Research, Vol. 3, No. 1, pp. 60-95.
Department of Trade and Industry (1991), Information Technology Security Evaluation Criteria (ITSEC), Department of Trade and Industry, pp.164.
Ein-Dor, P. et al. (1981), “Use of Management Information Systems: an empirical study”, paper presented at Second International Conference on Information Systems, Cambridge, Massachusetts, Dec. 7-9, 1981.
Franz, C. R.; Robey, D. (1986), “Organizational context, user involvement, and the usefulness of information systems”, Decision Sciences, Vol. 7, No. 3, pp.329-56.
Grover, V. et al. (1996), “Information systems effectiveness: the construct space and patterns of application”, Information & Management, Vol. 31, pp. 177-91.
Hitt, L.; Bryjolfsson, E. (1996), “Productivity, Business Profitability, and Consumer Surplus: Three Different Measures of Information Technology Value”, MIS Quarterly, Vol. 20, No. 2, pp. 121-42.
Igbaria, M.; Tan, M. (1997), “The consequences of information technology acceptance on subsequent individual performance”, Information & Management, Vol. 32, pp. 113-21.
Lewis, B. R. et al. (1995), “An Empirical Assessment of the Information Resource Management Construct”, Journal of Management Information Systems, Vol. 12. No. 1., pp. 199-223.
Mahmood, M. A. (1987), “System development methods – a comparative investigation”, MIS Quarterly, Vol. 11, No. 3, pp.293-311.
Miller, J. (2007), “Criteria for evaluating RFID Solutions for records and information”, Information Management Journal, ABI/INFORM Global, Vol. 41, No. 1, pp.50-3.
Miller, J.; Doyle, B. A. (1987), “Measuring the effectiveness of computer-based information systems in the financial services sector”, MIS Quarterly, Vol. 11, No. 1, pp.107-24.
Millman, Z.; Hartwick, J. (1987), “The impact of automated office systems on middle managers and their work”, MIS Quarterly, Vol. 11, No. 4, pp.479-91.
Moore, G. C. et Benbasat, I. (1991), “Development of an Instrument to Measure the Perceptions of Adopting an Information Technology Innovation”, Information Systems Research, Vol. 2, No. 3, pp. 193-222.
Morey, R. C. (1982), “Estimating and Improving quality of information in a MIS”, Communications of the ACM, Vol. 25, No. 5, pp.337-42.
Petter, S. et al. (2008), “Measuring information system success: models, dimensions, measures, and interrelationships”, European Journal of Information Systems, Vol. 17, pp. 236-63.
Petter, S.; McLean, E. (2009), “A meta-analytic assessment of the DeLone and McLean IS success model: An examination of IS success at the individual level”, Information & Management, Vol. 46, pp. 159–66.
Remus, W. (1984), “An Empirical investigation of the impact of graphical and tabular data presentations on decision making”, Management Science, Vol. 30, No. 5, pp.533-42.
Ribeiro, P. C. C. et al. (2009), “Application of an IT Evaluation Method”, International Journal of e-Business Management, Vol. 3, No. 2, pp. 20-38.
Ribeiro, P.C.C. et al. (2011), “The Application of RFID in Brazilian Harvest Facilities: Two Case Studies”, International Journal of Engineering Business Management, Vol. 3, No. 1, pp. 57‐63.
Rivard, S.; Huff, S. L. (1984), “User developed applications: evaluation of success from the DP Department Perspective”, MIS Quarterly, Vol. 8, No. 1, pp.39-50.
Rogers, E.M. (1995), Diffusion of innovations, 4 Ed., The Free Press, New York.
Rossi, R. M. (2008), “Método para análise interna das organizações: uma abordagem a partir da Resource-Advantage Theory”, Tese de Doutorado em Engenharia de Produção, Universidade Federal de São Carlos, São Carlos, São Paulo, SP.
Sabherwal, R. et al. (2006), “Information System Success: individual and organizational determinants”, Management Science, Vol. 52, No. 2, pp. 1849-64.
Santos, J. R. A. (1999), “Cronbach's Alpha: A Tool for Assessing the Reliability of Scales”, The Journal of Extension, Vol. 37, No. 2, pp. 1-4.
Sedera, D. et al. (2004), “A factor and structural equation analysis of the enterprise systems success measurement model”, paper presented at Twenty-Fifth International Conference on Information Systems, Washington, DC, 12-15 dec., 2004.
Slevin; D.P. et al. (1991), “Critical success factor analysis for information system performance measurement and enhancement - A case study in the university environment”, Information&Management, Vol. 21, pp. 161-74.
Sonnenwald, D. H. et al. (2001), “Using innovation diffusion theory to guide collaboration technology evaluation: work in progress”, in: Enabling Technologies: Infrastructure for Collaborative Enterprises – Tenth IEEE International Workshop on..., Wet Ice, Cambridge, EUA, 20-22 jun., 2001.
Srinivasan, A. (1985), “Alternative measures of system effectiveness: associations and implications”, MIS Quarterly, Vol. 9, No. 3, pp.243-53.
Tallon, P. et al. (2000), “Executives perceptions of the business value of information technology: a process-oriented approach”, Journal of Management Information Systems, Vol. 16, No. 4, pp. 145-73.
Voss, C. et al. (2002), “Case research in operations management”, International Journal of Operations & Production Management, Vol. 22, No. 2, pp. 195-219.
Wang, Y. D.; Forgionne, G. (2008), “Testing a decision-theoretic approach to the evaluation of information retrieval systems”, Journal Information Science, Vol. 34, No. 6, pp. 861-76.
Yin, R. K. (2001), Estudo de caso: planejamento e métodos, 2nd ed., Bookman, Porto Alegre.
Received: Aug 19, 2017
Approved: Jan 29, 2018
DOI: 10.14488/BJOPM.2018.v15.n1.a3
How to cite: Ribeiro, P. C. C.; Batalha, M. O.; Chudoba, K. M. et al. (2018), “Identification technologies evaluation method: an application in cattle chain”, Brazilian Journal of Operations & Production Management, Vol. 15, No. 1, pp. 23-34, available from: https://bjopm.emnuvens.com.br/bjopm/article/view/385 (access year month day).